Smart contract bug bounties have become a vital line of defense for Web3 projects aiming to secure decentralized applications before attackers strike. These programs attract thousands of researchers who probe code on blockchains such as Ethereum, Solana, and others. Real-world impact is clear: DeFi platforms routinely recover millions in potential losses, and governance protocols detect critical flaws before exploitation. Two industry cases: one protocol paid over $1 million to discover a reentrancy issue before deployment, and another prevented a multi-million token drain via a vulnerability disclosed through a bounty. Continue reading for a detailed dive into the latest statistical trends.
Editor’s Choice
- In H1 2025, smart contract bugs accounted for about $263 million in damages across Web3.
- Over $65 million was paid in bug bounties in 2023 for blockchain and smart contract vulnerabilities.
- Web3 platforms experienced over $3 billion in cumulative losses during H1 2025, marking one of the worst half-year periods to date.
- On average, critical bug reports on Immunefi command a minimum payout of $10,000.
- In 2025’s OWASP Smart Contract Top 10, Access Control Vulnerabilities rank as the top issue.
- Using static + completeness analysis, researchers disclosed 10 bug bounties totaling over $3 million in a recent automated vulnerability detection study.
- Approximately 85–90% of programs operate both public and invite-only private tracks, depending on project sensitivity.
Recent Developments
- Web3 lost $3.1 billion in H1 2025, marking the worst half since early 2023.
- Of that, $1.83 billion stemmed from access control exploits.
- AI-driven exploits surged by 1,025%, largely from insecure APIs and inference setups.
- A first major Uniswap V4 hook exploit led to a $12 million loss.
- Immunefi’s Q1 2025 “Hack3d” report documented 197 Web3 security incidents, with losses exceeding $1.6 billion across DeFi, NFT, and layer-1 protocols.
- Only 0.38% of stolen funds were recovered during Q1 2025, compared with 42.09% in the prior year.
- Smart contract bugs in 2025 contributed to a disproportionate share of overall Web3 damage.
Smart Contract Developer Salaries
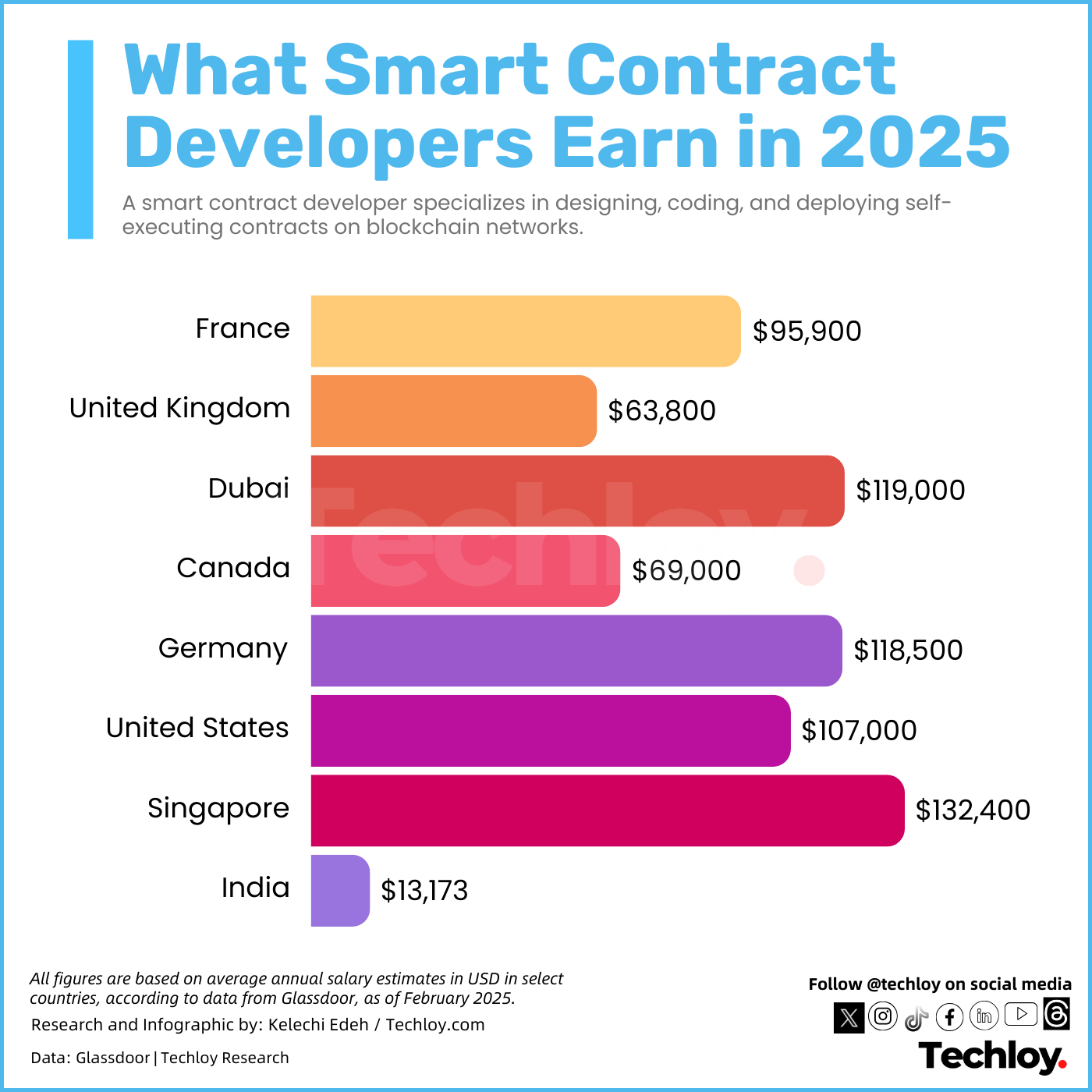
- In France, smart contract developers earn an average of $95,900 annually.
- In the United Kingdom, the average salary is around $63,800.
- Developers in Dubai earn among the highest, with an average of $119,000.
- In Canada, the average salary is $69,000.
- Germany offers an average of $118,500 per year.
- In the United States, developers earn about $107,000.
- Singapore leads globally with the highest average at $132,400.
- In India, salaries are significantly lower at $13,173 annually.
Overview of Smart Contract Bug Bounty Programs
- Bug bounty programs let independent security researchers find vulnerabilities in live or pre-deployment code and get rewarded for valid reports.
- They function as crowdsourced penetration testing specifically tuned for blockchain logic.
- Many programs are hosted on third-party platforms that manage report triage, payout logic, and scope definitions.
- Programs can be public or private/invite-only, depending on researcher access.
- Bug bounties complement traditional auditing and formal verification, catching issues that humans or tools might miss.
- The scope usually defines which contracts, functions, or modules are in-scope vs out-of-scope, protecting against spam submissions.
- Valid reports often require proof-of-concept exploits and clear reproduction steps.
- Because smart contracts are immutable post-deployment, finding bugs beforehand is critical; bug bounties help shift risk earlier.
Global Market Size for Smart Contract Bug Bounties
- In 2023, $65 million was disbursed across bug bounties in blockchain ecosystems.
- As of 2025, many Web3 projects earmark 5–10% of their security budgets toward bug bounty programs.
- HackenProof lists 200+ active Web3 bug bounty programs paying out over $15.7 million in total.
- Audit competitions like Immunefi’s smart contract library attracted reward pools of $21,000 for limited windows.
- Platform fees, triage costs, and reward payouts combine to make bug bounty infrastructure a multi-million-dollar sub-market.
- With savvy automation and tooling, platforms aim to scale while controlling false positives.
Web3 Security Report Losses
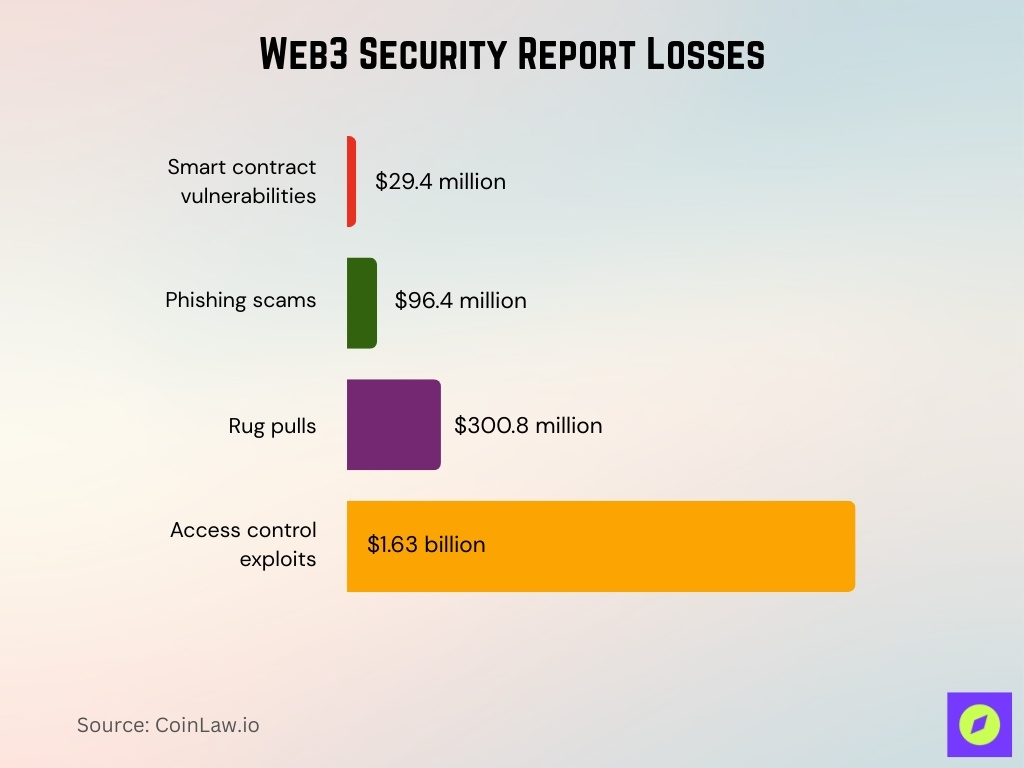
- The total Q1 2025 Web3 losses reached a staggering $2.05 billion.
- Access control exploits accounted for the largest share with losses of $1.63 billion.
- Rug pulls resulted in losses of around $300.8 million.
- Phishing scams caused damages totaling $96.4 million.
- Smart contract vulnerabilities contributed $29.4 million in losses.
Platforms and Projects Offering Smart Contract Bug Bounties
- Immunefi is among the leading Web3 security bounty platforms. It offers minimum rewards for critical smart contract bugs at $10,000.
- HackerOne runs a dedicated blockchain bug bounty program.
- HackenProof lists 200+ active Web3 bounty scopes with tens of thousands of reports.
- Many DeFi protocols and layer-1 blockchains host their own internal bounty programs.
- Platforms typically handle report triaging, severity grading, duplicate filtering, and payout escrow functions.
- Bugcrowd also accommodates blockchain clients.
- Some platforms run audit competitions and timed bounty events.
- Projects often combine audits + bounty + monitoring in layered security strategies.
Program Participation Statistics (Researchers, Reports, Programs)
- In Q1 2025, 197 security incidents were documented across Web3.
- On HackenProof, over 25,000+ reports have been received to date.
- Around 200 blockchain-related bug bounty programs were studied in a recent survey.
- A typical bug bounty program sees 50–70% of submissions rejected as duplicates or false positives.
- Many active platforms, about 88%, run both public and private programs.
- Researchers rank monetary incentive as the top motivator for participation.
- The number of participating researchers ranges from a few dozen to several hundred per program.
- Many hunters cite poor responsiveness or grading disputes as barriers.
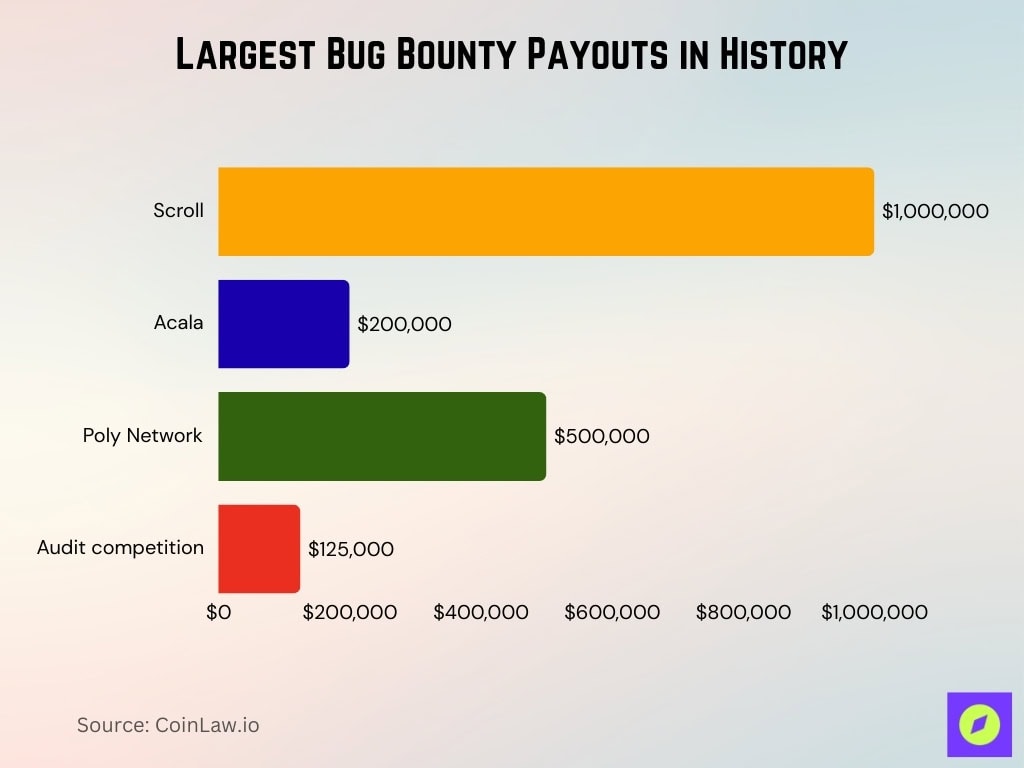
Largest Bug Bounty Payouts in History
- Scroll’s program allows payouts up to $1,000,000.
- Acala’s program caps at $200,000 for critical bugs.
- Some reentrancy exploit discoveries have fetched six-figure awards.
- Poly Network’s disclosure to a white hat included a $500,000 reward.
- Large audit-competition pools have awarded $125,000 in single events.
- These payouts can rival institutional audit budgets.
- Some bounty awards remain confidential but set benchmarks.
Adoption Rates of Bug Bounty Programs Across Blockchains
- On Ethereum, bug bounty payouts exceeded $7.6 million over the past 12 months.
- Cardano’s official bug bounty program offers rewards of up to $100,000 for critical vulnerabilities.
- Over 330 projects now rely on Immunefi’s bounty infrastructure.
- The Scroll layer-2 chain set a critical bug bounty cap at $1,000,000.
- Acala’s bug bounty program rewards critical vulnerabilities up to $200,000.
- In the broader bug bounty industry, Blockchain projects command ~$13,000 average for critical severity.
- Blockchain and DeFi projects now make up about 9% of all programs on major platforms.
- In 2025, simple smart contract exploits are expected to decline partly due to bug bounties and audits becoming standard.
Number of Critical Bugs Reported and Fixed
- Automated techniques uncovered 10 high-value vulnerabilities, totaling $3 million in bounties.
- Across all Immunefi payouts, 77.5% of bounties go toward smart contract bug reports.
- Many programs cap critical smart contract bug payouts at $50,000, with a minimum of $10,000.
- Scroll’s bounty cap for critical bugs is $1,000,000.
- The median payout among confirmed reports on Immunefi is around $2,000.
- Many valid submissions are duplicates or low severity; only a small fraction are critical.
- Audit competitions also discover critical vulnerabilities missed in audits.
- Many critical vulnerabilities are not disclosed publicly due to private bounties.
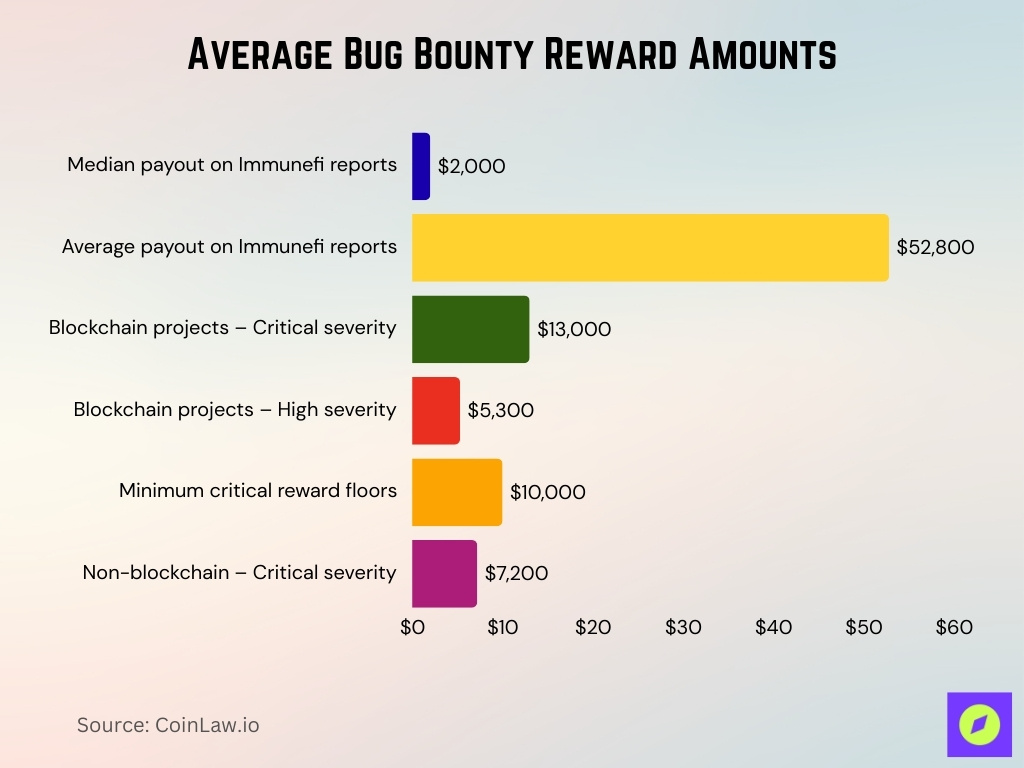
Average Bug Bounty Reward Amounts
- Median payout on Immunefi confirmed reports is around $2,000, while the average is ~$52,800.
- For blockchain projects, average critical-severity rewards were ~$13,000, high-severity ~$5,300.
- Many programs set minimum critical reward floors at $10,000.
- In non-blockchain programs, average critical rewards are about $7,200.
- A small number of critical payout accounts account for a large share of the distribution.
- Average payouts rise over time as budgets expand.
Severity Distribution of Reported Bugs
- Access Control vulnerabilities are the costliest, associated with $953.2 million in losses.
- Logic errors account for $63 million in losses.
- Reentrancy attacks remain a top-tier threat.
- Flash loan attacks cause damage in the tens of millions.
- Critical bugs may represent under 5% of total reports but receive a large share of payouts.
- High-severity bugs frequently drive mid-tier reward levels.
- Medium and low severity findings make up the bulk of reports.
- Inconsistent state update vulnerabilities were confirmed in 116 instances across 352 projects.
Financial Losses Prevented by Bug Bounty Programs
- Immunefi programs have saved projects more than $25 billion in potential losses.
- Bug bounties have prevented “billions in losses” by encouraging disclosure.
- In 2025, scaling rewards to funds at risk is becoming common.
- Hacken noted $2 billion+ lost in Q1 2025 that stronger bounty programs might have prevented.
- FailSafe’s 2025 report tallied > $2.6 billion in losses across 192 incidents.
- Access control flaws caused $953.2 million in losses, targeted by bounties.
- Logic flaws caused another $63 million in damages.
- Chainlight cited $84.8 million lost from logic bugs and $81.5 million from input validation flaws.
Time-to-Resolution for Submitted Vulnerabilities
- Critical submissions are often triaged within 48 hours, with all bugs reviewed in 5 days.
- Some platforms set a 14-day SLA for payout decisions.
- HackerOne’s Temu program averages ~1 day to first response, ~2 weeks to triage, and ~2 weeks to bounty decision.
- HackerOne’s X program averages ~1 day, 7 hours to first response, ~6 days, 9 hours to triage, and ~1 week, 16 hours to bounty decision.
- Research shows that patching delay is key to program efficiency.
- Ambiguous reports often stall patching.
- Hunters report that fixes may revert or not fully resolve the bug.
- Many blockchain programs face stricter resolution constraints due to immutability.
Real-World Case Studies: Successful Smart Contract Bug Bounties
- A DeFi lending protocol’s oracle logic flaw was flagged pre-launch, averting a $30 million drain.
- An NFT auction platform fixed a reentrancy vulnerability before repeated fund drains.
- A real estate tokenization protocol fixed a faulty access control before go-live.
- 116 inconsistent state update vulnerabilities were confirmed across 352 projects.
- 59% of contract transactions involve multiple contracts, enabling inter-contract exploits caught by bounties.
- The LLM-BSCVM framework improved detection and repair, supporting bounty outcomes.
- Formal verification + bounty disclosure prevented multi-million dollar exploits.
- Audit competitions publicly reward critical findings otherwise missed.
Trends in Smart Contract Bug Bounty Participation
- Immunefi’s total payout crossed $100.21 million, with 87.8% of bounties critical.
- The number of Web3 bug bounty scopes continues to grow year over year.
- Researchers increasingly use LLMs + automation tools for faster discovery.
- Cross-chain and modular designs encourage multi-chain bounty participation.
- Audit firms and bounty programs are collaborating more closely.
- Programs are adopting dynamic risk-based reward models tied to funds at risk.
- Private invite-only bounty tracks are growing.
- Projects are improving researcher experience through clearer scope and faster responses.
- Duplicate and low-value submissions persist but are being reduced with better tools.
Impact of AI and Automation in Vulnerability Detection
- The LLM-BSCVM framework achieved > 91% detection accuracy with only 5.1% false positives.
- A checker flagged issues in 64 GitHub projects, with 19 project owners confirming findings.
- Automated tools assist in triaging reports and ranking severity.
- Platforms integrate AI assistants to improve report quality.
- Automation detects shallow bugs earlier, leaving deeper flaws to humans.
- AI struggles with semantic vulnerabilities and cross-contract logic.
- The combined human + AI approach is proving most effective.
- Average detection time for low-severity bugs is decreasing due to automation.
Regulatory and Compliance Statistics
- Regulatory penalties for financial institutions rose 417% in H1 2025, totaling $1.23 billion.
- 32 U.S. states recognize smart contracts as legally binding, with 18 states considering legislation.
- The EU’s MiCA regulation, effective in 2025, mandates the enforceability of smart contracts.
- 60% of disputes are resolved through private arbitration.
- The average settlement amount in 2025 reached $1.2 million, up 15% from 2023.
- Only 12% of litigation cases are resolved in favor of the plaintiff.
- 58% of smart contracts now include compliance audit trails.
- 77% of organizations report improved compliance transparency with blockchain contracts.
- Regulatory pressure is pushing projects to tie bounty programs into compliance regimes.
Frequently Asked Questions (FAQs)
Immunefi has paid $100.21 million in total bounties, with 77.5 % going to smart contract bug reports.
Immunefi sets a minimum reward of $10,000 and a maximum cap of $50,000 for critical smart contract vulnerabilities.
Smart contract bugs caused approximately $263 million in damages in H1 2025.
In a recent program analysis, automated techniques disclosed 10 high-value bug bounties totaling over $3 million.
Researchers confirmed 116 inconsistent state update vulnerabilities across 352 smart contract projects.
Conclusion
Smart contract bug bounties have matured from niche experiments into core pillars of Web3 security. They have likely prevented billions of dollars in losses, caught critical vulnerabilities early, and spurred adoption of stronger security practices. The evolving interplay of AI, automation, and human insight is raising the bar for what bug bounty programs can catch. Still, faster resolution processes and regulatory alignment remain work in progress. In the full article, we’ll further analyze adoption trends, cross-blockchain comparisons, and forecast how smart contract security will evolve in the coming years.