One of DeFi’s oldest protocols, Yearn Finance, is facing scrutiny after an attacker exploited a legacy yETH token contract, minting trillions of fake tokens and draining millions in real assets from Balancer liquidity pools.
Key Takeaways
- An attacker exploited Yearn Finance’s legacy yETH token, minting 235 trillion tokens in one transaction.
- Roughly $9 million in total losses were confirmed by Yearn, with $3 million worth of ETH laundered through Tornado Cash.
- Yearn’s V2 and V3 Vaults were not affected by the exploit, and the issue remains isolated to an older yETH implementation.
- The protocol is working with SEAL 911 and ChainSecurity on a full post-mortem.
What Happened?
Yearn Finance confirmed on Sunday that its legacy yETH product was targeted in a sophisticated exploit. The attacker used a vulnerability in the token’s minting logic to create a nearly unlimited supply of yETH, then swapped the fake tokens for real assets from Balancer liquidity pools. Blockchain data shows the attacker minted around 235 trillion yETH tokens in a single transaction, draining millions in a matter of minutes.
We are investigating an incident involving the yETH LST stableswap pool.
— yearn (@yearnfi) November 30, 2025
Yearn Vaults (both V2 and V3) are not affected.
Yearn’s Legacy Token Exploited
The vulnerability was tied to an outdated version of the yETH token contract, not the newer vault infrastructure that Yearn currently promotes. By leveraging a flaw in this contract, the attacker was able to mint an infinite amount of yETH, which was then used to siphon off real ETH and popular liquid staking tokens (LSTs) from the associated Balancer pools.
- Blockchain analysis estimates the attacker made off with roughly $9 million, including $8 million from the yETH stableswap pool and $0.9 million from the yETH-WETH pool on Curve.
- Yearn confirmed that no other Yearn products, including V2 and V3 Vaults, were affected.
- Protocols like Katana, which rely on Yearn V3, also reported no exposure to the exploit.
According to Yearn, “Initial analysis indicated this hack has a similar high complexity level to the recent Balancer hack,” and investigations are underway with assistance from SEAL 911 and ChainSecurity.
Tornado Cash Used to Obscure Funds
Shortly after the exploit, the attacker moved quickly to obfuscate their trail. Around 1,000 ETH, worth approximately $3 million, was funneled through privacy protocol Tornado Cash in several batches, including multiple 100 ETH transactions. This pattern was flagged by blockchain observers such as Togbe and confirmed by Nansen alerts.
Several helper smart contracts were deployed moments before the exploit to facilitate the attack. These contracts self-destructed afterward, erasing on-chain evidence and complicating forensic analysis.
Not the First Time for Yearn
Yearn has dealt with security issues before. In 2021, the protocol lost $11 million from its yDAI vault, and in late 2023, a faulty script caused the loss of 63 percent of a treasury position, although no user funds were affected in that case.
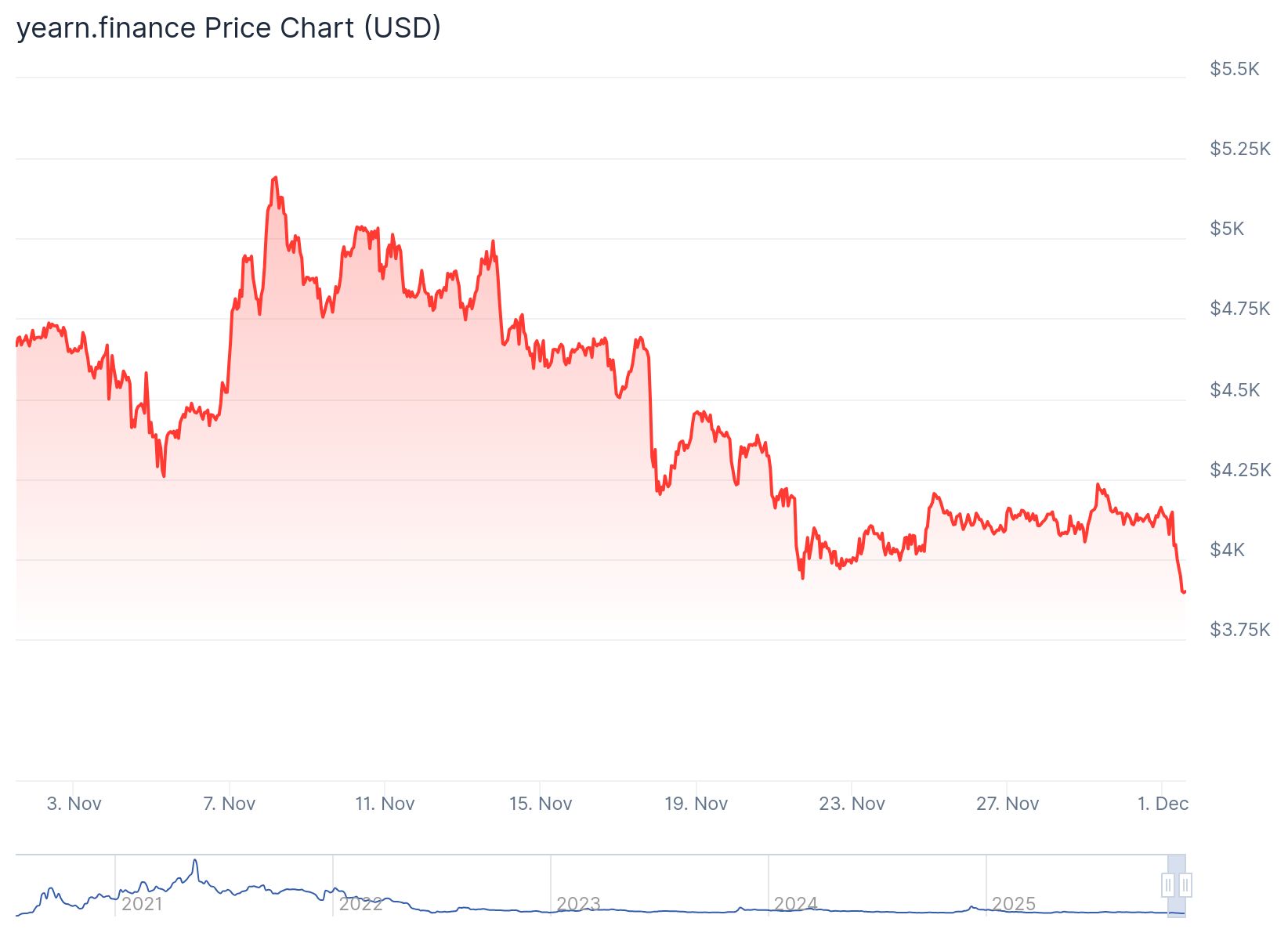
Despite the incident, Yearn’s Total Value Locked (TVL) remains above $600 million, suggesting its core systems are still trusted by many DeFi users. However, its governance token YFI saw a temporary drop of 4 percent, trading near $4,002 shortly after the exploit and currently trading at $3,898.
CoinLaw’s Takeaway
I’ve seen many DeFi exploits over the years, but this one stands out for how cleanly it separated old code from current infrastructure. What this tells me is that legacy risks never really go away, especially in protocols with long histories and evolving codebases. The fact that Yearn isolated the issue quickly and maintained trust in its newer vaults is a positive sign, but it’s also a wake-up call for every DeFi protocol to retire or harden old contracts. In my experience, it’s not always the flashy new code that gets exploited. Sometimes, it’s the forgotten bits that come back to bite.