Ransomware has dominated the malware landscape due to the recent spate of high-profile attacks. However, that does not imply that other cyber-attack forms and techniques are no longer dangerous. Some are still actively used and unsafe, although they might not carry the aura of infamy and renown they once did.
One of them is the botnets, which are responsible for various types of attacks.
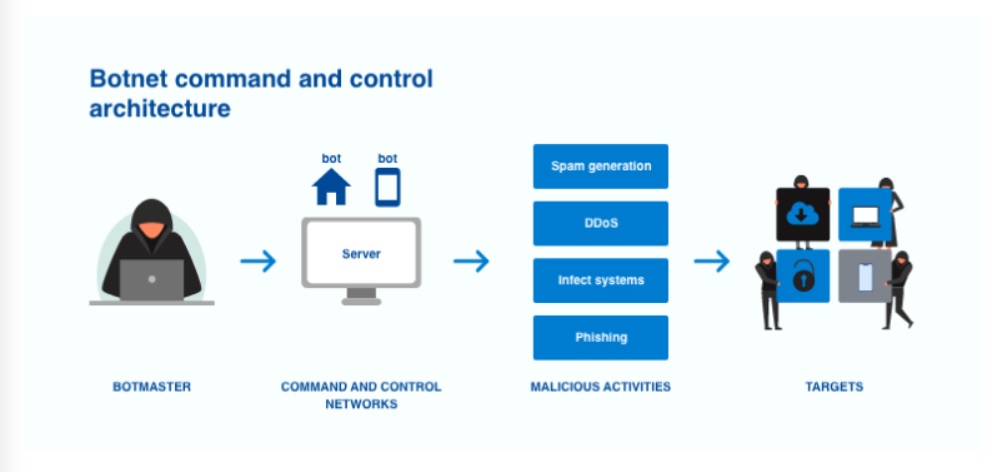
So what exactly is a botnet? The simple definition of a botnet is an inter-connected network of devices infected with malware used for cybercrime activity.
A botnet is a type of malware that can infect your computer and make it a “zombie.” It may sound frightening, but it is essential to be aware of this threat to protect yourself. What is a botnet, and how does it work?
There are several types of botnets, and they can be used for different purposes. Let’s take a closer look at how this ubiquitous form of malicious software works.
How Do Botnets Work?
Botnet is a combination of the words “robot”, “network” and “robot”. Botnet attacks are automatically carried out by computers connected to the network. Therefore, the term “robot” is also included in the name. Botnets infect PCs and other devices that are connected to the internet. Each afflicted device is added to the network.
Any form of malware planting could infect the botnet’s initial features. Hackers could use software vulnerabilities, weaknesses in cyber security, and email to carry out this activity. Once a botnet group has been established, it is able to “recruit” additional devices into the “robot network.
Many botnet-affiliated PC users are unaware that their computer is infected. They seek out other devices to infect their computers, rather than brains. Computers in a botnet are often referred to as “zombie armies” because they serve evil intently.
How are Botnet Commands Issued?
Botmasters and bot herders are the names given to owners of bot networks. The bot herder is responsible for managing the botnet remotely using command and control (C2 servers or C&C servers). A botnet server can be used to issue commands to the network. Each zombie computer affected must comply with those commands.
Hackers might use various command-issuing methods. IRC channels used to be the most popular method of sending commands in the past. After being infected, devices would join an IRC channel. After infecting a device, the creator of the bot would use the channel to send commands and instruct the gadgets on what they should do.
This method of sending commands via IRC channels also falls under the umbrella of centralized botnets, also known as client-server botnets. In a centralized botnet framework, the bot herder communicates directly with each zombie device.
These botnets are easier to set up and make it simpler for government agencies and cybersecurity companies to identify the botnet owners. Most hackers prefer the decentralized botnet structure.
The bot herder is able to issue commands to infected gadgets within the peer-to-peer, decentralized botnet. There are thousands of devices infected. The instructions are then sent to all remaining members of the botnet by the initial command recipient.
This makes it much more difficult to identify the source of the botnet commands, which can make it harder to shut down the network and bring criminal charges against its creator.
Zeus, the most well-known botnet, was also able to shift from a central to a decentralized model in order to continue its operations. Zbot, or Zeus, a very sneaky botnet that appeared in 2007
Zeus was the largest botnet in history with 3.6 million bots within its network in 2009. It was used to steal financial information and add more bots to its network.
In 2010, the Zeus botnet was shut down. A new version of the botnet, GameOver Zeus appeared. This transitioned from a centralized botnet architecture to a decentralized one. We continue to be troubled by the adaptations of Zeus and his many offspring.
Types Of Botnet Attacks
Okay, now that we understand the basics of how botnets are created and how they work, a question remains: What purposes do botnets serve?
Botnets can be used to launch malware attacks. They rely on the sheer number of zombie computers within their ranks to overwhelm a computer system, crash down a network, flood the internet with email, and force it offline. Let’s look at some of the most famous cases of each type of attack.
DDoS Attacks – Because of how botnets work (which provide bot herders a forceful army of conscripts), the cybercriminals who control them employ the network to carry out attacks that can take advantage of their numerical superiority. One of the best types of attacks to win is DDoS attacks.
DDoS stands as Distributed Denial of Service. These attacks attempt to overwhelm a network, server, or service with traffic. This is done by sending a large number of access requests to it. The target will then go offline and become unreachable to other users.
Furthermore, DDoS attacks offer botnet owners an opportunity to attack their network with the help of thousands of zombie devices. DDoS attacks using botnets tell all devices in the network to attack a specific service or website by sending requests. The goal is to slow it down or bring it down to a crawl.
DDoS botnet attacks are also used to intimidate and blackmail companies in order to extort a ransom.
Mirai was a particularly vicious botnet that made use of DDoS attacks. In 2016, the aforementioned botnet launched DDoS assaults that temporarily blocked access to the majority of the internet on the US East Coast.
Along with its adverse effects, what made this attack unique was the presence of numerous Internet of Things (IoT) devices among the botnet’s 600,000 infected machines. This was the first instance of an IoT device being attacked; until now, cybercriminals have only targeted infecting computers.
Moreover, Mirai’s original purpose was not as evil as you might think. This is an interesting fact. They weren’t cybercriminals trying to extort money from government sites; they were children looking for DDoS Minecraft servers to get an edge in the game.
Email Spam – Email spam is one of the oldest and most prevalent botnet attacks. Botnet spam attacks use thousands of zombie devices to send large numbers of emails in a short time. This can serve multiple purposes and be used to perform various tasks, including overloading an individual’s email inboxes to disseminating malware and phishing scams.
Khan C. Smith’s botnet attack in 2000 was one of the most prominent. Smith was able to send around 1.25 million phishing emails using the spam botnet that he created.
These emails were intended to steal credit card information and other sensitive data. Smith was successful and managed to grab upwards of $ 3 million. That is until he was arrested by law enforcement and sued for roughly $25 million.
Cutwail was another well-known botnet that specialized in spam email. 51 million emails were sent every minute by the Cutwail botnet in 2009, accounting for a staggering 46.5% of all spam sent worldwide at the time. Cutwail used DDoS assaults in addition to email spam. The botnet is still thought to be alive even if its activity has drastically decreased over time.
Identity theft and information theft – Owners of botnets also engaged in more traditional methods of cybercrime. Bot herders frequently use botnets to access enterprise systems to steal information from the targeted business and its customers. The botnet would attempt to scrape financial and personal information, which would then be exploited or sold for profit.
Cryptocurrency Mining – Most of today’s well-known cryptocurrencies are created using a procedure called mining. The GPU or CPU of a computer is used in cryptocurrency mining to tackle challenging mathematical puzzles. Computers are infected and added to a crypto mining botnet by malicious actors looking to steal coins.
These crypto botnets allow bot herders to save their resources and make money by having instant access to thousands upon thousands of involuntary mine rigs.
Furthermore, the unprecedented growth in crypto-related activity has made crypto botnets more popular over the years. A crypto botnet’s owner can also evade prosecution and identification due to the anonymity of its crypto transactions.
Sysrv, first identified in December 2020, is one of the most potent crypto botnets. Additionally, Sysrv is a highly advanced botnet that mainly targets enterprise-level applications.
It can attack Windows and Linux systems, create more hacker bots, and even track down and remove other crypto-mining malware. In addition, it can search the system for private keys that would enable it to propagate throughout the entire network. Sysrv is still highly active as of 2021.
Bricking – Since Mirai, IoT devices such as different sensors, voice-control hardware, and home security systems have become popular targets for botnets. If IoT device owners were curious about botnets, they quickly learned the truth. Bricking is one popular type of attack that targets IoT device owners. It wipes a device’s firmware, making it permanently unusable.
How To Remove A Botnet And Protect You Against Botnet Attacks
Although botnets sound frightening and can certainly cause damage if left unchecked, computer users and businesses are not defenseless. Here are the most effective ways to defend yourself from botnet attacks.
- Install the best antivirus software and keep it up-to-date.
- Be sure to double-check any suspicious-looking emails before you open them.
- If you aren’t sure what the attachments are or if the sender is legitimate, don’t download them.
- Don’t click on links that look suspicious.
- Use strong passwords on all your smart devices.
- Keep your device’s firmware up to date.
Conclusion
A botnet is a cyber attack technique that allows attackers to remotely control infected devices to launch massive cyber attacks. Using a botnet, attackers can exploit thousands of devices at once, making it difficult for defenders to track and stop the attack. Organizations and individuals should take steps to protect themselves from botnet attacks by using strong passwords, updating software regularly, and using security software.
ABOUT AUTHOR
Over 4 years’ experience in the research industry. Experience with research and consulting projects, catering to domains such as ICT, Health & Pharma, and packaging. Managed projects on both B2B as well as B2C perspectives, which includes consumer preference analysis, interviews with key executives, etc